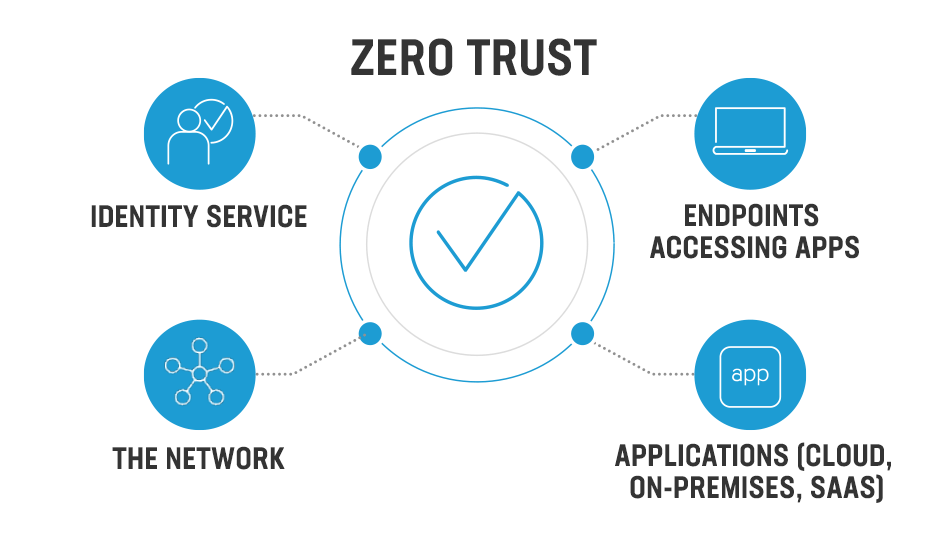
Zero trust is a security model that assumes that an attacker is already inside the network and seeks to limit the damage that an attacker can do. It is not just about securing the perimeter of the network, but also about securing the internal network and the endpoints. This is because in today's digital world, the perimeter is no longer defined by the physical boundaries of the office, but by the devices and networks that employees use to access company resources.
One of the key components of zero trust is identity and access management. This includes using multi-factor authentication (MFA) to secure access to company resources. MFA requires users to provide not just a password, but also a second form of authentication, such as a fingerprint, a token, or a code sent to a mobile device. This makes it much more difficult for attackers to gain access to your resources, even if they have stolen a user's password.
Another important component of zero trust is network segmentation. By segmenting your network into different zones, you can limit the amount of damage that an attacker can do in the event of a breach. For example, you can create a DMZ (demilitarized zone) where public-facing resources, such as web servers and email servers, are located. This limits the amount of damage that an attacker can do if they are able to compromise one of these servers.
Continuous monitoring is another important aspect of zero trust. By monitoring your network and resources in real-time, you can quickly detect and respond to security incidents, such as a breach or a malicious insider. This allows you to minimize the amount of damage that an attacker can do, and also helps you to recover more quickly from a security incident.
In addition, another important component of zero trust is micro-segmentation. This is the process of breaking down your network into small segments, so that you can control access to specific resources on a per-user or per-device basis. This allows you to limit the amount of damage that an attacker can do in the event of a breach, as well as to detect and respond to security incidents more quickly.
With all these security measures in place, it is important to have a team of experts who can help you implement and maintain them. That's where a managed IT services provider like Titan Tech comes in. Titan Tech has the expertise and resources to help your business implement zero trust by implementing the security measures mentioned above and will be able to monitor and maintain them, so you can focus on your business.
In conclusion, zero trust is a comprehensive security model that is becoming increasingly important for businesses of all sizes. It is not just about securing the perimeter of the network, but also about securing the internal network and the endpoints. Titan Tech can help your business implement zero trust by implementing security measures such as multi-factor authentication, network segmentation, continuous monitoring, and micro-segmentation and will be able to monitor and maintain them, so you can focus on growing your business.